|
Access Control System Introduction Access is access control, people in and out when the channel is important, the appropriate level of permissions identification to distinguish whether through a management tool.
Generally can be identified by the person's identity password, card, fingerprint, iris (eye), also on behalf of the bearer of the authority.
Access control system is the alternative key functions in a common entrance, to grant everyone the keys are inconvenient to deal with people leaving the job, the key is lost, identity registration records tracking has great difficulty; if you send someone to guard the presence of high cost, difficult to manage, there is the possibility of favoritism. Access control system a good solution to these problems is a basic requirement of modern social work situations, but also the direction of development.
Access control system in China after 10 years of development, has been very mature and stable, installation, service, prices are more suitable for large-scale uses. In Shenzhen and other coastal cities, access control system has been installed it is common for a company's needs, factories and so on. 
Access Control System Classification Access control systems generally have the following types: 1, no network access control, machine management is a one door, can not be controlled by computer software, you can not see the record, directly controlled by the controller. Characterized by cheap, simple installation and maintenance, you can not view the record, not for the number of people who are often more than 50 or flow (often refers to someone entry and exit) where the number of gates is not suitable for more than 5 projects.
2,485 network access control, and the computer that can access the type of communication directly using software management, including cards and event control. So there are easy to manage, centralized control, you can view the records, the records analysis and processing for other purposes. Characterized by a relatively high price, it does increase the installation and maintenance, but simple training, attendance and other value-added services can be carried out. For many people, mobility, multi-door project.
3, TCP / IP access, also known as Ethernet network access control, also can be networked access control system, but through the network cable to the computer and networking controllers. In addition to having all the advantages of 485 networked access, it also has a faster, easier installation and greater number of networking can be cross-regional or inter-city network. But there are high equipment prices, the need for a computer network knowledge. Suitable for installation in large projects, more than the number of people on the required speed, cross-regional projects.
4, fingerprint access control system, is replaced by a fingerprint card access control management devices, it has the same characteristics as 485, but with better security, the drawback is the small number of people registered by slow. 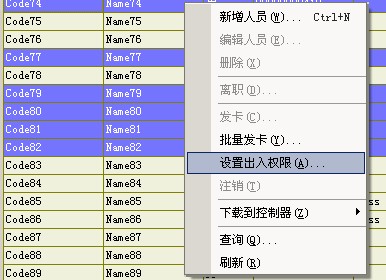
Typical application The following description of the various types of application access control system, basically have the following seven kinds of access does not mean that only these types of use. These types can be used independently or in combination, depending on the project requirements change, flexible use of various programs is one of the characteristics of our access control system.
If necessary, these systems can also be composed of more complex applications, such as anti-absconds, interlocking, multi-regional multi-machine management, etc. A typical application - the basic structure of the basic access control applications, the use of 485 controllers, readers , converters, locks, power supplies. A typical application - Basic access control structure The most basic application, the use of 485 controllers, readers, switches, locks, power supplies. 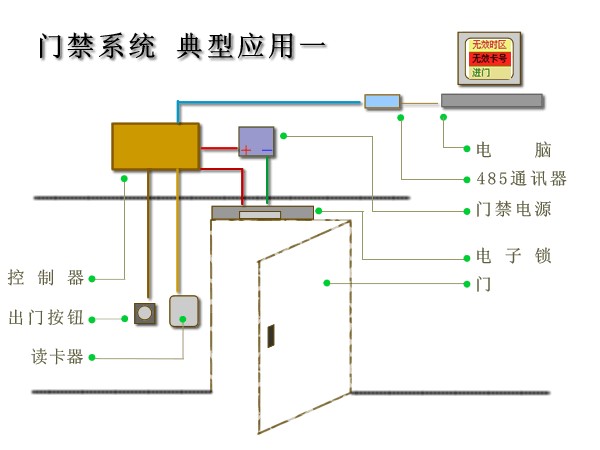
·Having access basic functions
• Basic Networking System
• Only one or two read
•low cost
• With this chart, you can understand the basic access control system
========================================= Application Object • Access to the less demanding, the need for basic card management, credit card record entry events, the situation is only one of the number of installations.
• Management card is relatively small.
• performance critical. B Typical applications - Primary network access control structure 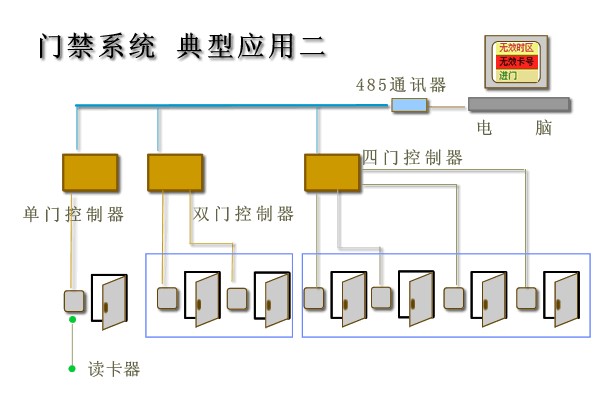
·Having access basic functions
·A variety of 485 models of network access control
• Each controller is connected to the reader and buttons and other external devices
• Convenient networking, easy to control costs
• All controllers are connected via a communication device to the computer 485, the controller can be expanded to add more
• Wiring, see each door of a typical application.
========================================== Application Object ·Access to less demanding, the need for basic access control capabilities, record credit card records of the project, the number of installed units in many cases.
• All the doors in a relatively close range.
Compare the use of multi-door near the door controller, single-door distant door controller.
• On the performance of less demanding, less management card. C Typical applications - Multi-interface access control structure 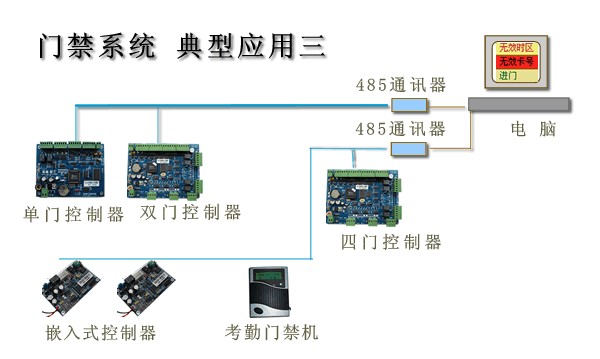
·Multiple networked access controller 485 models
• Connect to the computer through a plurality of 485
• Excellent communication, performance
• Convenient networking, easy to control costs
• Can be expanded more than 485 converters
Typical application wiring, see each controller
========================================== Application Object ·The number of gate management more, need more access control functions.
• All the doors in a relatively close range.
• A variety of models mix and cost savings.
• A variety of models used in combination, perform different functions.
• Multiple interfaces to use, easy wiring.
• Performance critical, management card 4,000 or less. D Typical applications - the basic structure of Ethernet Access 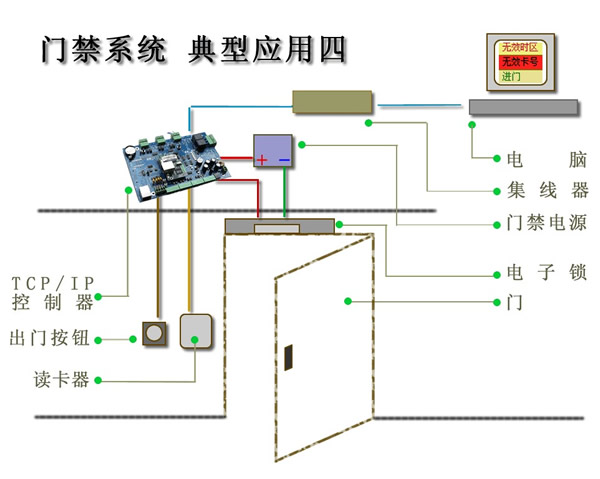
· The controller is connected directly to the computer via a hub
• Convenient networking, quick installation and maintenance
• You can use a variety of other TCP / IP Controller Model
• You can have the optional door sensor, alarm, fire alarm, output devices and other accessories
========================================== Application Object ·The number of managed less than four doors.
• All the doors in a relatively close range.
• Controller to have more ready-made computer network cable, or local area network within the company already has.
• The need higher performance.
• Controlled door is not local, it needs to be managed remotely over the network.
• Reach 20,000 times. E Typical applications - Ethernet Access extension structure 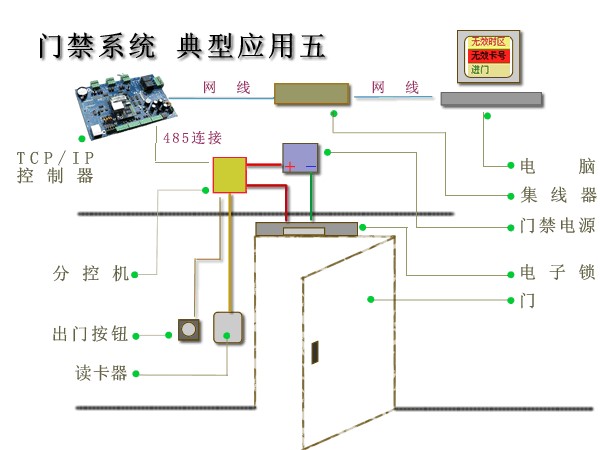
·The basic structure of the two Ethernet networking • Using the optional "sub-control modules" to facilitate the installation and wiring, control module and access points connected to the motherboard are equivalent.
·The controller is connected directly to the computer via a hub
• Convenient networking, quick installation and maintenance
• You can use a variety of other TCP / IP Controller Model
• You can have the optional door sensor, alarm, fire alarm, output devices and other accessories
========================================== Application Object ·Some doors in a distant place, the use of WG reader convenient wiring, using sub-control machine.
• Lock, reader, buttons can be connected to the sub-control module above.
• Sub-control module to the host is 485, it can be up to 1200 meters away.
• Controller to have more ready-made computer network cable, or local area network within the company already has.
• The need higher performance.
• Controlled door is not local, it needs to be managed remotely over the network.
• Reach 20,000 times. F Typical applications - Extended Access Control Structure 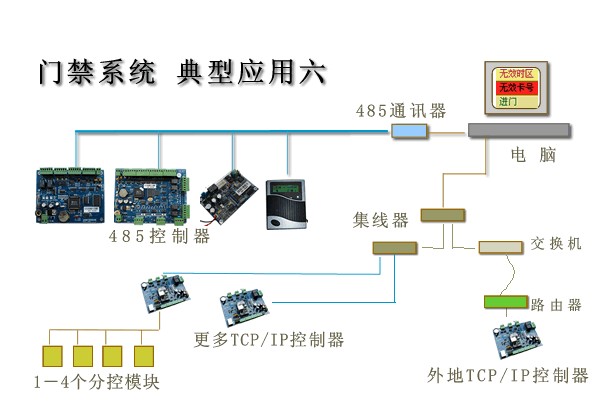
·Integrated Application • Access Control System
·a variety of models, a variety of types of access control in combination, including the controller 485 and TCP / IP controller.
• TCP / IP controller option "sub-control module."
• Remote TCP / IP controller is connected via a wide area network.
• All devices through a software management system, to achieve a variety of applications.
• convenient networking, quick installation and maintenance.
• All controllers can use any host 1-4 door models
• You can have the optional door sensor, alarm, fire alarm, output devices and other accessories
========================================== Application Object ·Some doors in a more distant places, such as in other cities.
• Some doors in distant places, such as other floors or other floor.
• Use WG reader convenient wiring; or insufficient wire, can no longer increase the line where the use of sub-control machine
• controller to have more ready-made computer network cable, or local area network within the company already has.
• require higher performance.
• require multiple applications. G Typical Application - Access Control Software Structure 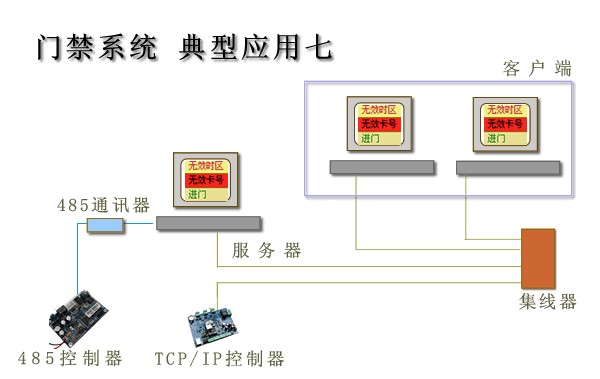
·Integrated application access control system
·A variety of types of controllers used in combination
• Multiple computers simultaneously control, real-time display.
• Multi-division personnel management responsibilities.
• Multi-language, multi-database system.
• Attendance software has the same network structure.
• All devices through a software management system, to achieve a variety of applications.
• Real-time display of all computer records, and can control the door switch
========================================== Application Object ·Management personnel quantity.
• Management personnel division of power, different people manage different content, such as time and attendance data management, card, access authorization, records inquiries.
• The structure can be used in any of the previous six programs.
|